Researchers and Academics from one university in the Netherlands and ETH Zurich, Switzerland, have published details about a new security vulnerability affecting all Intel processors.
Dubbed as CrossTalk, this new vulnerability can be used to leak data across all CPU cores. It enables attacker-controlled code executing on one of the CPU cores to leak any sensitive data from other software which is running on a different CPU core.
The Vrije University’s Systems and Network Security Group (VUSec) claim that the CrossTalk vulnerability is another type of MDS (microarchitectural data sampling) attack. MDS attack which was announced by Intel in 2019 is composed of related technologies such as ‘Zombie Load’ and ‘Fallout’, and it may cause attacks such as CacheOut and LVI leading to data leakage.
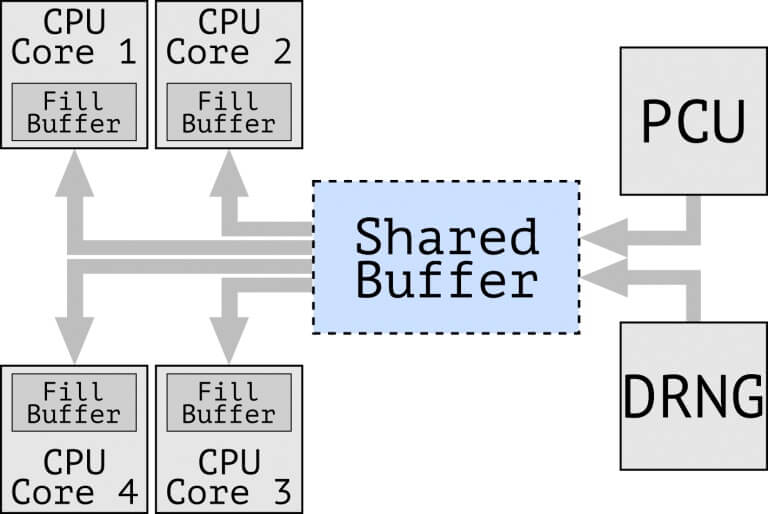
MDS attacks usually target the user data while in a ‘transient’ state, but CrossTalk attacks data while it’s being processed by the CPU’s Line Fill Buffer (LBF), one of the CPU cache systems. According to VUSec, the LBF cache actually works with a previously undocumented memory staging buffer that is shared by all the CPU cores.
Until now, all the attacks assumed that attacker and victim were sharing the same core, so that placing mutually untrusting code on different cores would thwart such attacks. Now the researchers have presented a new transient execution vulnerability, which Intel refers to as “Special Register Buffer Data Sampling” or SRBDS (CVE-2020-0543), enabling attacker-controlled code executing on one CPU core to leak sensitive data from victim software executing on a different core.
CrossTalk is actually trying to bypass all patches against Spectre and Meltdown so it can attack any CPU core. It enables an attacker-controlled code execution on one CPU core to leak sensitive data from victim software executing on a different core. This technique can be quite dangerous especially for cloud shared systems. So even if Hyper Threading is disabled and with prior mitigations, Intel CPUs can still be exposed to CrossTalk. SRBDS is similar in nature to MDS (Microarchitectural Data Sampling) but with this important difference.
(SRBDS) vulnerability is about instructions that perform off-core accesses to shared buffers. Among the instructions vulnerable to SRBDS is RDRAND and RDSEED, which can be problematic due to the often sensitive nature of needing secure random number generation. The CPUs which have been affected by this vulnerability span from Intel Skylake to Coffee Lake. Intel’s Cascade Lake appears to be the first generation not vulnerable to cross-core attacks.
Mitigating this CrossTalk involves locking the entire memory bus before updating the staging buffer and unlocking it after the contents have been cleared. Most of Intel’s recent products are not vulnerable to this attack, since the chipmaker has made some significant changes to the hardware design. But for the older Intel CPU lineup, the chipmaker has today released microcode (CPU firmware) updates to patch this CrossTalk vulnerability.
As with any side-channel attacks reported till this day, Intel is not aware of any real-world exploits of SRBDS outside of a lab environment, Intel said in a blog post when analyzing its June security updates.
You can find the full list of vulnerable Intel CPUs on this page (please kindly check the SRBDS column). The list covers CPUs for embedded, mobile, desktop, and server products.
VUSec academics have also published a proof-of-concept code and a technical paper as well. Intel’s own technical write-up can be viewed here.
Diagram showing the Flow via shared staging buffer to fill buffers of specific cores.
UPDATE:
The original article stated that CrossTalk affects all Intel processors. Apparently, though, CrossTalk does not affect all of them. Here is the list of affected processors. Moreover, here is a statement from Intel.
“Special Register Buffer Data Sampling (SRBDS) is similar to previously disclosed transient execution vulnerabilities and does not impact many of our most recently released products, including Intel Atom processors, Intel Xeon Scalable Processor Family and 10th Generation Intel Core processors. For those processors that may be affected, we coordinated with industry partners to release microcode updates that address these vulnerabilities. For more information, please see our developer resources.”
Hello, my name is NICK Richardson. I’m an avid PC and tech fan since the good old days of RIVA TNT2, and 3DFX interactive “Voodoo” gaming cards. I love playing mostly First-person shooters, and I’m a die-hard fan of this FPS genre, since the good ‘old Doom and Wolfenstein days.
MUSIC has always been my passion/roots, but I started gaming “casually” when I was young on Nvidia’s GeForce3 series of cards. I’m by no means an avid or a hardcore gamer though, but I just love stuff related to the PC, Games, and technology in general. I’ve been involved with many indie Metal bands worldwide, and have helped them promote their albums in record labels. I’m a very broad-minded down to earth guy. MUSIC is my inner expression, and soul.
Contact: Email